Posted by: Roberto Bulla, Senior Software Architect, Engineering Sardegna
and Glauco Mancini, Senior Solution Architect, Engineering Sardegna
and Antonio Salis, R&D Project Manager, Engineering Sardegna
and Shirley Crompton, Senior Researcher, UKRI/STFC
What is a blockchain?
In his essence Blockchain is an immutable record or ledger used to track and manage the story of asset ownership with triple-entry accounting. Another core component of blockchain technologies is cryptography, this enables the passing of confidential information in the presence of adversaries, bad actors or simply audiences with no need to know. Signing transactions cryptographically also helps guarantee authenticity. Finally, blockchain makes extensive use of peer-to peer network architectures increasing redundancy or availability and fault tolerance by removing single points of failure. All these technologies existed from a long time. Ledger exists from 5.000 B.C. in the single entry version, and from 1340 A.D. in the double-entry version. In 1973 asymmetric cryptography was born and in 2001 Bit-torrent came with the wide adoption of the peer-to-peer networks.
The story of blockchain begins with a whitepaper published by an anonymous author, Satoshi Nakamoto, a decade ago in 2009. The ideas outlined in this whitepaper led to the world’s first and largest Blockchain: Bitcoin. Bitcoin is a cryptocurrency that keeps its users highly anonymous through public key infrastructure (PKI) and cryptographic hashing. PKI is built on asymmetric cryptography, which uses a pair of reciprocal keys (public and private) to encrypt and decrypt secret records. In a Bitcoin Blockchain, users store their virtual bitcoins in a digital wallet that contains the account’s private key, which is used to sign all transactions from that account. Conversely, all transactions presented by that account will be verified by the Bitcoin network using the account’s corresponding public key. Since participants don’t trust each other, especially in a public Blockchain with anonymous users, consensus algorithms like Proof of Work (more explanation later) are used to approve new insertions into the ledger.
It is important to note that while anonymity is not a blockchain requirement, many platforms, especially those aimed at business and enterprise use, like the Linux Foundation Hyperledger Fabric and R3 Corda, supports user identity. This allows solution architects and administrators to define and enforce permission- and role-based access control. In business scenarios, key features of public blockchains like user anonymity and full-transparency of the transactions are in fact less desirable as a user may not wish to reveal full details of a transaction to would-be competitors. However, a tamper-proof, append-only ledger is important to ensure that a transaction cannot be altered.
SIGNIFICANT BLOCKCHAIN DATES
- 2009 – First Bitcoin Block Created.
- 2010 – Satoshi Disappears in December – Date of last public post.
- 2015 – Ethereum, Public BlockChain with Smart Contract Capabilities, and Hyperledger, Private Blockchain Enterprise Class, both go live.
- 2018 – Demand for blockchain increases, 14 Open Jobs for every blockchain developer.
- 2019 – Walmart requires produce suppliers to deploy a blockchain solution.
- 2021 – Dubai hosts all government operations and record-keeping operations on blockchain as part of the Smart Dubai 2021 initiative.
Definition
Blockchain is a structure for storing data in a ledger in a way that is nearly impossible to change. It can be used to store digital representation of all kinds of valuable assets. Figure 1 summarises a Blockchain’s key features.
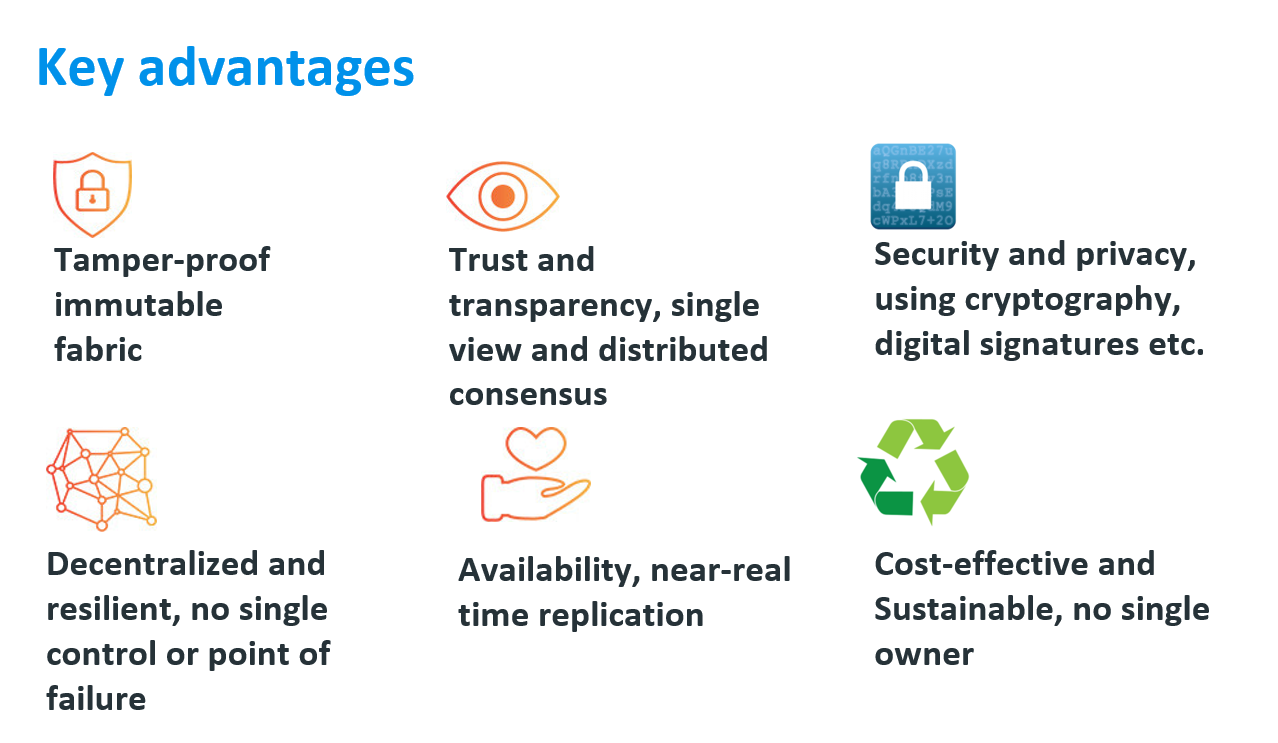
Figure 1 – Blockchain key features
What is blockchain for?
It’s a new way of answering an old question: how can we exchange something of value in a trustless environment?
- Enforcement
Early civilizations used threat of force and public shaming as retributions for dealing in bad faith when engaging in trade. Blockchain uses smart contracts to automate contract enforcement.
- Institutions
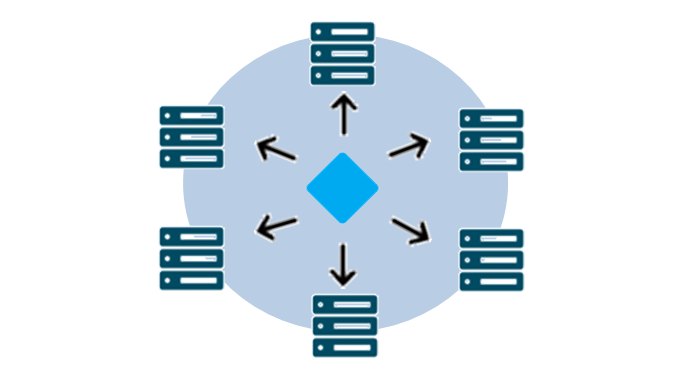
The emergence of governments and banks with organized, central authorities to which we could outsource trust as long as we trust them. Blockchain achieves trust via the consensus mechanism. A basic principle of Blockchain is that the networked nodes share a single view of the blockchain state; the nodes in effect police each other and they reconcile the distributed transactions at near realtime to achieve this single view.
- The Network
Blockchains distributed across thousands of computers can mechanize trust without the need of a centralized enforcement authority, opening the door to new ways of organizing “decentralized” enterprises and institutions across organizational boundaries on a shared interest basis.
Let’s look at the main five steps in a Blockchain transaction :
- A transaction is born
In Bitcoin, a transaction is the transfer of cryptocurrency from one person (Alice) to another (Bob). In Ethereum, which includes a built-in programming language that can be used to automate transactions, there are multiple possibilities. Alice can send cryptocurrency to Bob. Or someone can create a transaction that places a piece of code, a smart contract, on the blockchain. Alice and Bob can then send money to an account this program controls, if certain conditions encoded in the contract are met, the money is released. A smart contract can also send transactions to the blockchain in which it is embedded.
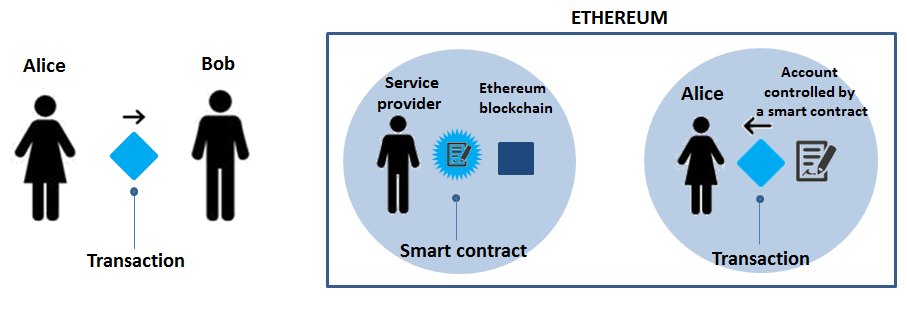
- The transaction is broadcast to a peer-to-peer network
Let’s say Alice wants to send some money to Bob. To do so, Alice creates a transaction on her computer that must reference a past transaction on the blockchain in which she received sufficient funds, as well as her private key to the funds and Bob’s address. That transaction is then sent out to other computers, or “nodes,” in the network. The nodes will validate the transaction as long as it has followed the appropriate rules, and have a majority Consensus. Then mining nodes (more on those in step 3) will write it to the chain.
- The race to create new blocks
A subset of nodes, called miners, organize valid transactions into lists called blocks. A block in progress contains a list of recent valid transactions and a cryptographic reference to the previous block. In blockchain systems like Bitcoin and Ethereum, miners race to complete new blocks, a process that requires solving a computationally challenging task (Proof of Work Consensus), which is unique to each new block. The first miner that solves the puzzle will earn some cryptocurrency as a reward. The math puzzle involves randomly guessing at a number called a nonce. The nonce is combined with the other data in the block to create an encrypted digital fingerprint, called a hash.
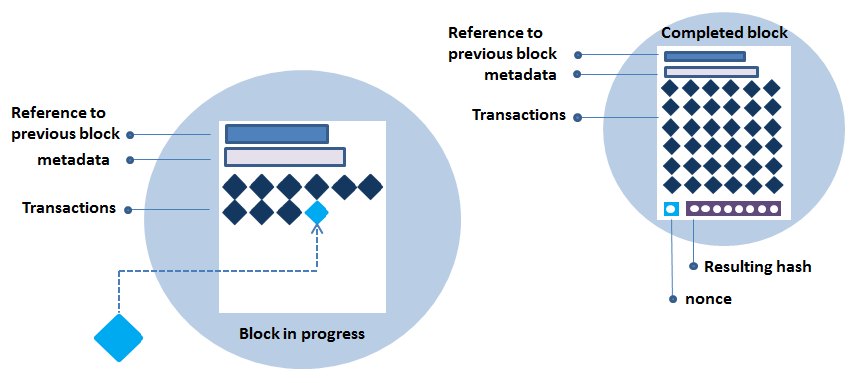
- Completing a new block
The hash must meet certain conditions; if it doesn’t, the miner tries another random nonce and calculates the hash again. It takes an enormous number of attempts to find a valid hash. This process deters hackers by making it expensive to modify the ledger. While some blockchain entities use other systems to secure their chains, this approach, called Proof of Work, is the most thoroughly battle-tested and often used in public blockchains.
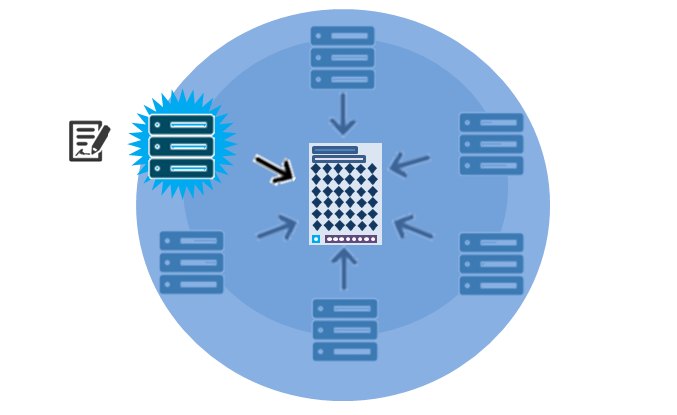
- Adding a new block to the chain
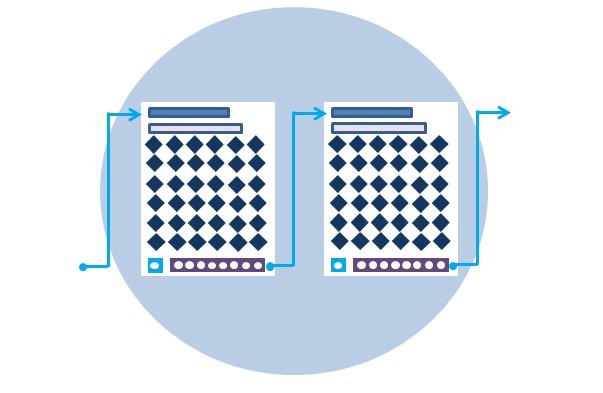
This is the final step in securing the ledger. When a mining node becomes the first to solve a new block’s crypto-puzzle, it sends the block to the rest of the network for approval, earning digital tokens in reward. Mining difficulty is encoded in the Blockchain’s protocol; Bitcoin and Ethereum are designed to make it increasingly hard to solve a block over time. Since each block also contains a reference to the previous one, the blocks are mathematically chained together. Tampering with an earlier block would require repeating the Proof of Work for all the subsequent blocks in the chain.
Using Blockchain within the mF2C project
Specifically to Use Case 3 Smart Fog-Hub Service (SFHS), we are investigating using Blockchain technology to manage coupons issued directly by the shop promotions in the airport. Here is an overview of the process:
1) The customer makes a purchase in an airport shop which offers promotion A
2) Airport shop A generates a specific coupon for the promotion, registered on a blockchain as a “smart contract”, valid for airport shop B for the specific customer
3) The customer goes to airport shop B and makes a purchase using the coupon generated in step (2)
4) The smart contract is automatically triggered and the revenue sharing policies are applied between the airport shops A and B.
Another relevant application of Blockchain relates to securing the mF2C platform itself. We have already outlined the key advantages of the Blockchain technology above. The various built-in security features like exploiting cryptography to ensure data confidentiality, integrity and authenticity etc., plus, key of all, the self-policing consensus mechanism, have attracted many to view Blockchain as a fitting solution for securing the highly distributed fog ecosystem where trust is lacking between peers.
For securing the mF2C platform, we are considering adopting Distributed Ledger Technology (DLT), a new generation of Blockchain technology that can be used to implement lighter weight, private permissioned blockchains without a cryptocurrency aspect. The technology supports a variety of simpler consensus protocols other than the compute-intensive Proof of Work algorithm for minting new transactions, e.g. Proof of Authority where an identified user (this needs not be a human user) is appointed to approve new transactions.
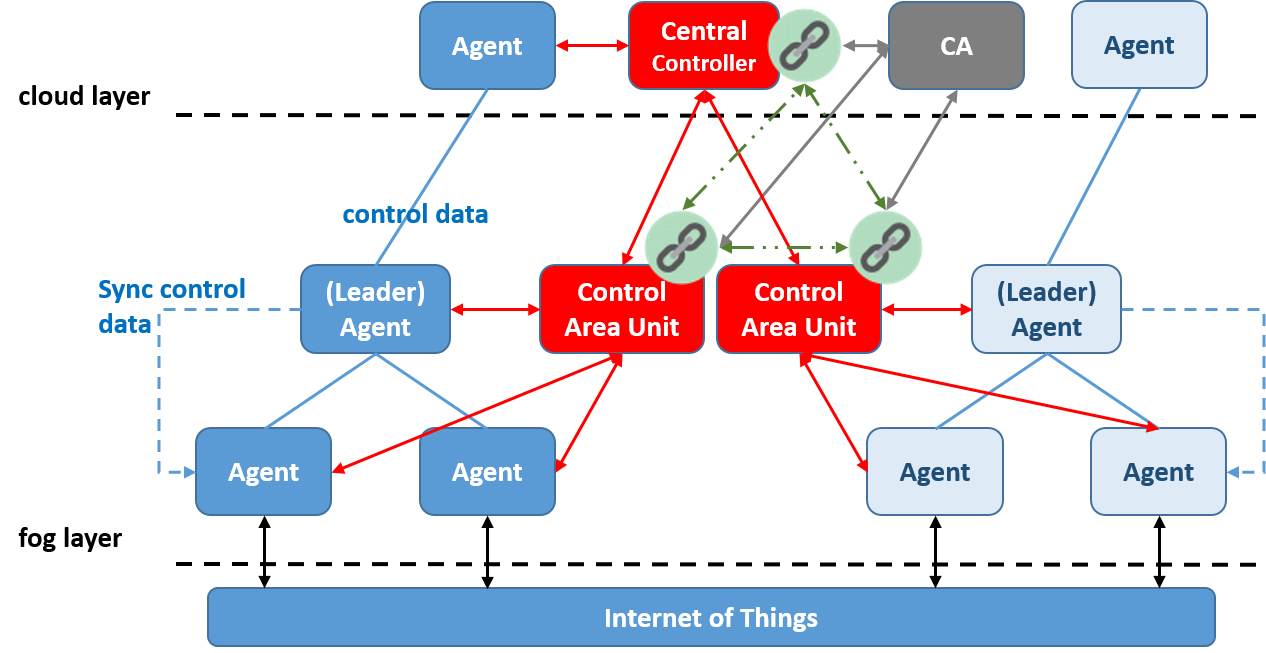
We intend to use DLT for bootstrapping trust in the mf2c infrastructure and deliver most of the security features currently provided by the Control Area Unit (CAU) security middleware. These include:
- a peer network of CAUs with built-in redundancy and availability of security data, such as Agent identities and fog membership,
- near-real time replication of security data across the CAU network to ensure availability to support low latency decision making,
- safeguarding the confidentiality of security data through access control and cryptography,
- protecting the integrity of security data via the blockchain tamper-proof fabric,
- ensuring data accountability through its immutable data structure,
- using automated smart contract to enforce user-defined policies at transaction time, e.g. controlling access, triggering notifications, revoke credentials, etc.
We envisaged that each distributed CAU would act as gatekeeper for its corresponding fog area (see figure below)and help new agents to join the mF2C blockchain network. Each CAU would be a node in the proposed blockchain network, storing Agent identity and fog membership information in its immutable fabric. Chain data would be replicated in near-real time to other nodes on the mF2C blockchain network to facilitate identity management, trust establishment, and the confidentiality, integrity and auditability of the security information.